고정 헤더 영역
상세 컨텐츠
본문
Normally your switch will automatically learn MAC addresses and fill its MAC address table (CAM table) by looking at the source MAC address of incoming frames and flooding frames if it doesn’t know where to forward the frame.
This process is vulnerable to layer 2 MAC address spoofing attacks where an attacker spoofs a certain MAC address to change entries in the MAC address table. A really simple method to deal with this issue is to manually configure entries in the MAC address table, a static entry will always overrule dynamic entries. You can either specify the interface where the MAC address is located or tell the switch to drop the traffic.
Let’s look at an example!


To demonstrate this we only require two devices. A router to generate some traffic and a switch to look at (and configure) the MAC address table. Here’s the configuration:
What would be ideal would be something like the 'show mac address-table interface' command, but for an interface range rather than a specific interface: This is the type of output I'm looking for, with each mac address listed for the port in question: switchxxx#show mac address-table interface g3/0/11 Mac Address Table-Vlan Mac Address Type. Layer 2 Learning and Forwarding for VLANs Overview, Layer 2 Learning and Forwarding for VLANs Acting as a Switch for a Layer 2 Trunk Port, Understanding the Unified Forwarding Table, Example: Configuring a Unified Forwarding Table Custom Profile, Configuring the Unified Forwarding Table on Switches, Configuring Forwarding Mode on Switches, Disabling Layer 2 Learning and Forwarding. Show mac address-table aging-time vlan vlan-id Syntax Description. Vlan vlan-id (Optional) Displays information for a specific VLAN only; the range of valid values is from 1 to 4094. Defaults None Command Modes Any command mode Supported User Roles.
We’ll do a quick ping to generate some traffic so SW1 can learn about the mac address of R1’s FastEthernet 0/0 interface:
Show Mac Address Table For Vlan Settings
Let’s take a look at the MAC address table:

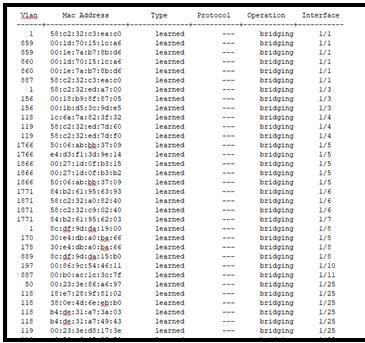
Here’s the MAC address of R1, learned dynamically. Let’s turn this into a static entry:
Show Mac Address Table For Vlan Setup
Use the mac address-table static command to create a static entry. Here’s what the MAC address table looks like now:
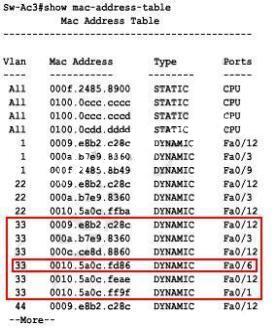
There it is, a static entry. No way to overrule this unless you have access to our switch. This prevents us from moving R1 to another interface on SW1 unless we change the static entry. Like I mentioned before we can also change a static entry so it will drop all traffic. Here’s how to do it:




